发表于: 2018-10-19 23:44:47
1 406
今天完成的事情:
1、今天计划写用户和权限相关模块,仔细缕了一下逻辑
用户登录 ——> 验证账号密码——>验证成功,发送账号密码到授权服务器获取Token——>拿着Token去访问相应的服务——>服务对token进行解析,获取相关用户信息——>根据用户信息判断该用户是否有相关访问权限。
2、搭建授权服务器
项目架构如下:
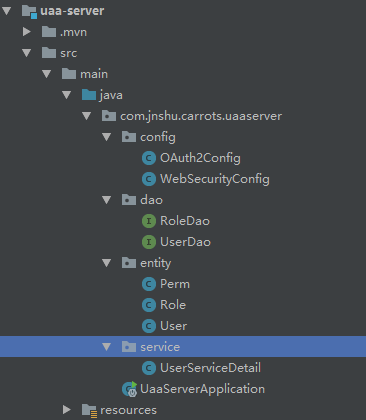
主要配置:
User实体类:
package com.jnshu.carrots.uaaserver.entity;
import org.springframework.security.core.GrantedAuthority;
import org.springframework.security.core.userdetails.UserDetails;
import java.io.Serializable;
import java.util.Collection;
import java.util.List;
import java.util.Map;
import javax.persistence.*;
@Entity
public class User implements Serializable, UserDetails {
@Id
@Column(name = "user_id", unique = true, nullable = false)
@GeneratedValue(strategy = GenerationType.IDENTITY)
private Long userId;
@Column(name = "user_name",nullable = false, unique = true)
private String username;
@Column(name = "user_password")
private String userPassword;
@ManyToMany(cascade = CascadeType.ALL, fetch = FetchType.EAGER)
@JoinTable(name = "user_role", joinColumns = @JoinColumn(name = "user_id", referencedColumnName = "user_id"),
inverseJoinColumns = @JoinColumn(name = "role_id", referencedColumnName = "role_id"))
private List<Role> roleList;
@Transient
Map role;
public User() {
}
public Map getRole() {
return role;
}
public void setRole(Map role) {
this.role = role;
}
public Long getUserId() {
return userId;
}
public void setUserId(Long userId) {
this.userId = userId;
}
public String getUserPassword() {
return userPassword;
}
public void setUserPassword(String userPassword) {
this.userPassword = userPassword;
}
public List getRoleList() {
return roleList;
}
@Override
public Collection<? extends GrantedAuthority> getAuthorities() {
return null;
}
@Override
public String getPassword() {
return userPassword;
}
@Override
public String getUsername() {
return username;
}
public void setUsername(String username) {
this.username = username;
}
public void setRoleList(List<Role> roleList) {
this.roleList = roleList;
}
@Override
public boolean isAccountNonExpired() {
return true;
}
@Override
public boolean isAccountNonLocked() {
return true;
}
@Override
public boolean isCredentialsNonExpired() {
return true;
}
@Override
public boolean isEnabled() {
return true;
}
}
UserServiceDetail
package com.jnshu.carrots.uaaserver.service;
import com.jnshu.carrots.uaaserver.dao.RoleDao;
import com.jnshu.carrots.uaaserver.dao.UserDao;
import com.jnshu.carrots.uaaserver.entity.Role;
import com.jnshu.carrots.uaaserver.entity.User;
import org.springframework.beans.factory.annotation.Autowired;
import org.springframework.security.core.GrantedAuthority;
import org.springframework.security.core.userdetails.UserDetails;
import org.springframework.security.core.userdetails.UserDetailsService;
import org.springframework.security.core.userdetails.UsernameNotFoundException;
import org.springframework.stereotype.Service;
import java.util.*;
@Service
public class UserServiceDetail implements UserDetailsService {
@Autowired
private UserDao userRepository;
@Autowired
private RoleDao roleRepository;
@Override
public UserDetails loadUserByUsername(String username) throws UsernameNotFoundException {
System.out.println("---------------"+username);
User user = userRepository.findByUsername(username);
List<Role> roleList= user.getRoleList();
Map roleMap = new HashMap(16);
List<Role> roles= new ArrayList<>();
for (Role authority : roleList) {
String role= authority.getRoleName();
Collection<? extends GrantedAuthority> authList= roleRepository.findByRoleName(role).getAuthorities();
roleMap.put(role,authList);
roles.addAll((Collection<? extends Role>) authList);
}
user.setRoleList(roles);
user.setRole(roleMap);
System.out.println(user);
System.out.println(roles.size());
return user;
}
}
package com.jnshu.carrots.uaaserver.config;
import com.jnshu.carrots.uaaserver.service.UserServiceDetail;
import org.springframework.beans.factory.annotation.Autowired;
import org.springframework.beans.factory.annotation.Qualifier;
import org.springframework.context.annotation.Bean;
import org.springframework.context.annotation.Configuration;
import org.springframework.core.io.ClassPathResource;
import org.springframework.security.authentication.AuthenticationManager;
import org.springframework.security.oauth2.config.annotation.configurers.ClientDetailsServiceConfigurer;
import org.springframework.security.oauth2.config.annotation.web.configuration.AuthorizationServerConfigurerAdapter;
import org.springframework.security.oauth2.config.annotation.web.configuration.EnableAuthorizationServer;
import org.springframework.security.oauth2.config.annotation.web.configurers.AuthorizationServerEndpointsConfigurer;
import org.springframework.security.oauth2.provider.ClientDetailsService;
import org.springframework.security.oauth2.provider.client.JdbcClientDetailsService;
import org.springframework.security.oauth2.provider.token.TokenStore;
import org.springframework.security.oauth2.provider.token.store.JwtAccessTokenConverter;
import org.springframework.security.oauth2.provider.token.store.JwtTokenStore;
import org.springframework.security.oauth2.provider.token.store.KeyStoreKeyFactory;
import javax.annotation.Resource;
import javax.sql.DataSource;
/**
* @Author 李景磊
* @Description
* @Date 2018/10/19 16:07
* @Param
* @return
*/
@Configuration
@EnableAuthorizationServer
public class OAuth2Config extends AuthorizationServerConfigurerAdapter {
@Override
public void configure(ClientDetailsServiceConfigurer clients) throws Exception {
clients.withClientDetails(clientDetails());
}
@Bean
public ClientDetailsService clientDetails() {
return new JdbcClientDetailsService(dataSource);
}
@Autowired
UserServiceDetail userServiceDetail;
@Resource
private DataSource dataSource;
@Override
public void configure(AuthorizationServerEndpointsConfigurer endpoints) throws Exception {
endpoints.tokenStore(tokenStore()).tokenEnhancer(jwtTokenEnhancer()).authenticationManager(authenticationManager);
endpoints.userDetailsService(userServiceDetail);
}
@Autowired
@Qualifier("authenticationManagerBean")
private AuthenticationManager authenticationManager;
@Bean
public TokenStore tokenStore() {
return new JwtTokenStore(jwtTokenEnhancer());
}
@Bean
protected JwtAccessTokenConverter jwtTokenEnhancer() {
KeyStoreKeyFactory keyStoreKeyFactory = new KeyStoreKeyFactory(new ClassPathResource("ljl-jwt.jks"), "ljl123".toCharArray());
JwtAccessTokenConverter converter = new JwtAccessTokenConverter();
converter.setKeyPair(keyStoreKeyFactory.getKeyPair("ljl-jwt"));
return converter;
}
}
3、学习了Mybatis的一个很牛逼的技能.——查询结果映射
可以直接将连表的结果映射出来
如:
ResultMap
<resultMap type="com.jnshu.carrots.adminservice.model.Ljl" id="userOrderitemsResultMap">
<id property="userId" column="user_id"/>
<result property="userName" column="user_name"/>
<result property="userPassword" column="user_password"/>
<collection property="roleList" ofType="com.jnshu.carrots.adminservice.model.Role">
<id property="roleId" column="role_id"/>
<result property="roleName" column="role_name"/>
<collection property="permList" ofType="com.jnshu.carrots.adminservice.model.Perm">
<id property="permId" column="perm_id"/>
<result property="permName" column="perm_name"/>
</collection>
</collection>
</resultMap>
SQL语句
SELECT
`user`.user_id,
`user`.user_name,
`user`.user_password,
perm.perm_id,
perm.perm_name,
role.role_id,
role.role_name
FROM
`user`
INNER JOIN user_role ON user_role.user_id = `user`.user_id
INNER JOIN role ON user_role.role_id = role.role_id
INNER JOIN role_perm ON role_perm.role_id = role.role_id
INNER JOIN perm ON role_perm.perm_id = perm.perm_id
WHERE
`user`.user_id = #{userId,jdbcType=BIGINT}
直接执行SQL语句时的结果
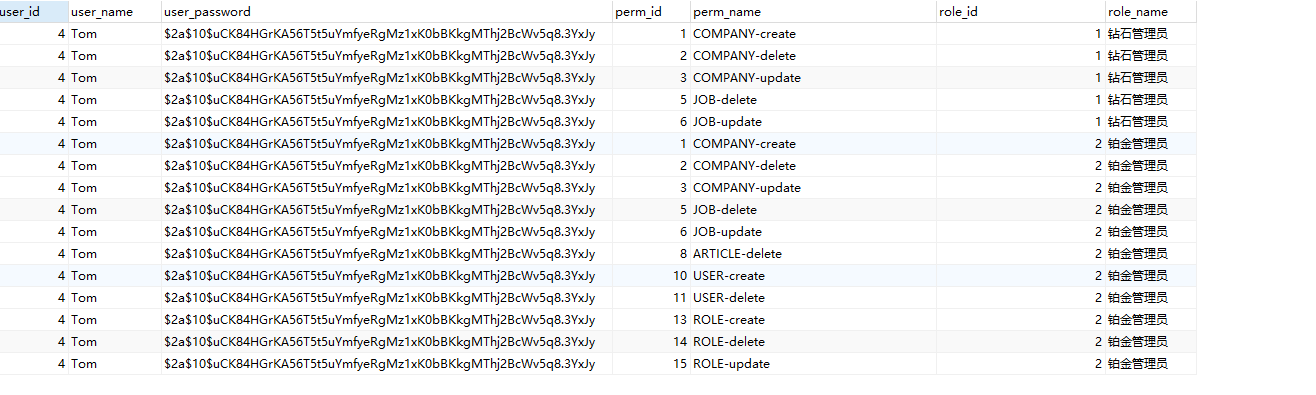
程序执行输出的结果
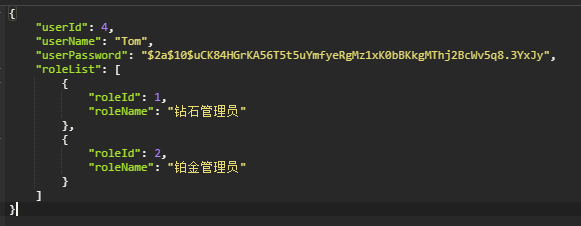
即Mybatis将结果自动进行了封装。
明天计划:
继续写用户模块和权限模块
遇到的问题:
暂无
收获:
以上





评论